Microsoft 365 Defender – Part 2
In this blog post, which is part 2 of a series (part 1 here), we will go a little more into some of the functionality in this product. Some of the more important features of new security products are the ones based on machine learning and AI. It is important to work on security skills, but when things happen so fast and on such a large scale, we can really use some help from the machines that are on our side. Microsoft Threat Intelligence analyzes 24 trillion signals daily and use machine learning and AI to react and respond to threats.
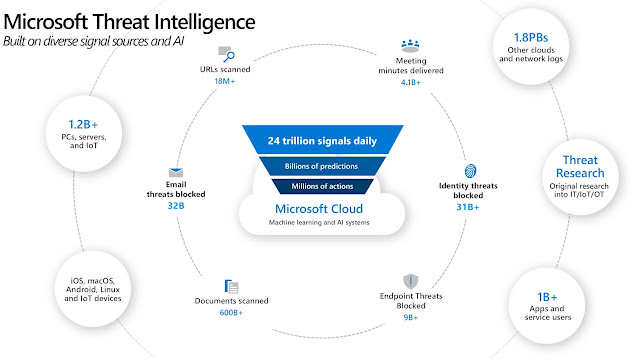 |
| Microsoft Threat Intelligence (aka.ms/mcra) |
This means that we in many cases can expect response times way beyond what even the best security teams can achieve.
Todays topic – Threat analytics
Today, as we continue our journey into the Microsoft 365 Defender product, we're going to talk about Threat analytics. This is an extremely useful feature which gives us insight into what's going on in the world, and if our environment is vulnerable to the ongoing threats. As Microsoft describes this:
Threat analytics is our in-product threat intelligence solution from expert Microsoft security researchers, designed to assist security teams to be as efficient as possible while facing emerging threats, including:
- Active threat actors and their campaigns
- Popular and new attack techniques
- Critical vulnerabilities
- Common attack surfaces
- Prevalent malware
This is an awesome one:
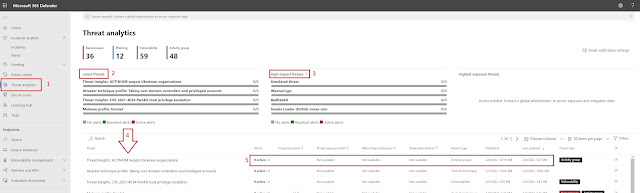 |
| Threat analytics pane |
- Threat analytics can be reached by selecting the option on the left. This will take us into the portal, and present us with a view of the current threat landscape.
- Latest threats shows us what new and dangerous in the world.
- High impact threats will show the really dangerous stuff. We also have a "Highest exposure threats" which in my case is empty. Normally you would see some products here, but things are calm and peaceful in my demo tenant.
- This is where it get's interesting. Below the mentioned columns we can see how this is impacting your environment.
- Let's say that we have some devices that are vulnerable to one of the threats, we can see that, and look into which devices are impacted, and how we can fix it.
 |
| Looking into one of the threats |
- The list of options will allow us to read detailed analyst reports, see which (if any) assets are impacted, and more.
- In my case there are no impacted assets, but if that is the case, you can view the impacted assets by selecting the View all impacted assets option.
- Exposure level is Low in my case. That is a good thing. In the example above there are no Misconfigured og vulnerable devices (yay), but if you do, you go to View exposure and mitigation details.
So, there you have it. A quick look at the Threat analytics pane. If you have the opportunity, go explore here, and see how things are in your tenant. I hope this has been useful and will have another post about Defender soon. If you look at the picture below, you will see many of the security features in Microsoft cloud. We will look at several of these in the coming weeks, but in the meantime I can recommend taking a look at Microsoft Cybersecurity Reference Architectures to gain more insight into this.



Comments
Post a Comment