Microsoft 365 Defender - part 1
Our journey to the cloud has created some new ways of thinking, new ways of working, and of course a bunch of new portals to work in. It's beginning to be a while since Microsoft started consolidating their different security products under the defender name. Some of the big ones like the Advanced Threat Protection solutions are well known to many of us and more products are being added under the Defender umbrella all the time. Today we are going to look at Defender for Microsoft 365. What it is, and how it can help us. My demo tenant has Microsoft 365 E5 licenses, and this gives us the full power of the defender suite.
What is the Microsoft 365 Defender product really?
In this post, which is part 1 in a series, we will look at some of the basics of Microsoft 365 Defender. Many of us are used to defining Microsoft 365 Defender from what we can see in the security.microsoft.com portal, where we can:
- Detect Security risks
- Investigate attacks
- Prevent harmful activities
And much more. A lot of the security stuff here will be done automatically. Microsoft has quite a few success stories (like the bad rabbit attack (Ransom:Win32/Tibbar.A – Protection in 14 minutes ) where we are protected in minutes, without any human intervention.
Microsoft 365 Defender is a collection of several products in what Microsoft calls a unified enterprise defense suite:
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps (Cloud App security)
Previously we have had to use many different portals for these products but these days it is all in the Microsoft 365 Security center. Here we can monitor and respond to threat activity and strengthen security posture across identities, email, data, endpoints, and apps. The gathering of all this info into one portal gives us a great overview of what's going on in our tenant.
Home
As we first look at security.microsoft.com we will see the different cards available to us.
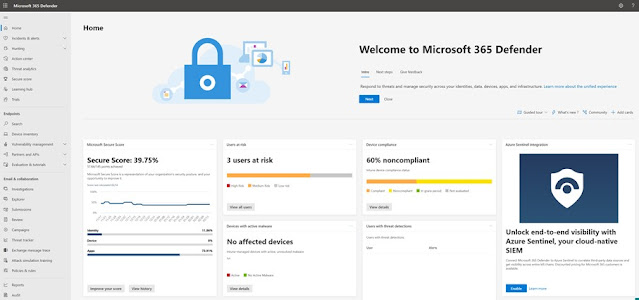 |
| Microsoft 365 Defender start page |
 |
| Improvement actions |
The view we first see in Microsoft 365 Security center is highly configurable. It is a collection of different cards (as they are called) and each of those cards contain a piece of information like Secure Score, Threat analytics, device compliance and much more. One of the great things about this is that we can add/remove "cards" as shown below. This way we can focus on what is important to us.
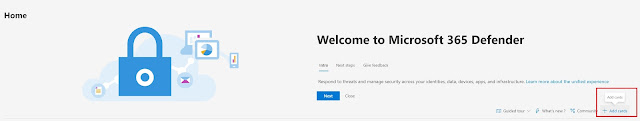 |
| Add remove cards |
 |
| Add a card |
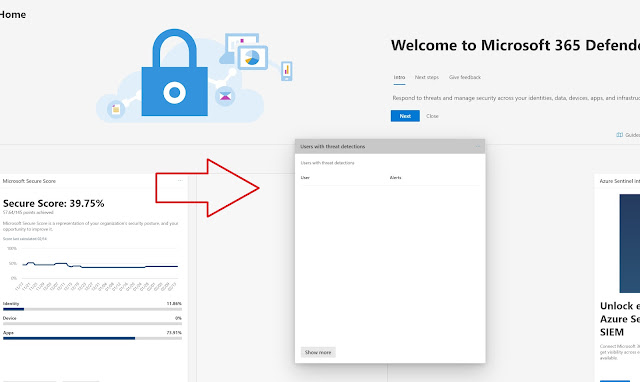 |
| Move cards around |
Incidents
 |
| Incidents & Alerts |
| An alert! |
 |
| Different types of info can be found by going into the alert. |
 |
| Looking at details. |
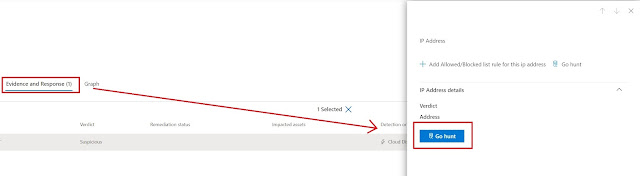 |
| Go hunting without a hunting license. |
 |
| Many possibilities in the Advanced hunting panel. |


Comments
Post a Comment