Using Secure Score and Compliance score to help secure your environment.
It is easy
to get lost wen looking through all the different security and compliance
settings in Microsoft 365. We see some truly scary stuff out there these days,
like what happened with Garmin who was basically shut down for days after a
ransomware attack.
First: Sorry I’ve been so bad at updating the blog lately. The current pandemic has kept my focus elsewhere. But as it seems this will be the new normal in the days to come, I have decided to start blogging more again.
Thankfully, when we put our stuff in the cloud, Microsoft has done a lot for us. Two services especially, should help us get started, and even guide us through some pretty deep configurations of security and compliance. Unfortunately for those of you who are not using E5 (or equivalent) licenses, you will miss out on some of the best security features out there.
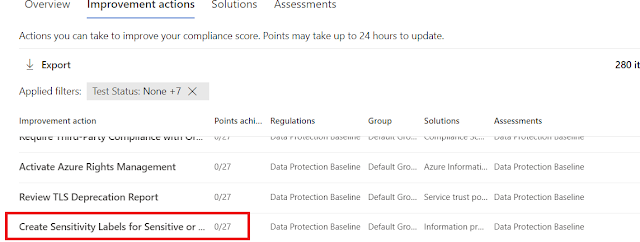
There are many interesting features here, and you can get a great overview of what is done, and what should be done. If we go to improvement actions, we can see a list of things that should/could be done, and also see how this is weighed.
As we can see here, MFA is at the very top, and this is an easy thing to implement, with enormous security gains. At the last (physical) ignite, we were told that only 8% of all tenants had enabled MFA for admins. Scary, but hopefully this is a lot better now.
This came a little later but is also extremely useful. Security and Compliance are two areas that hang together so closely that many of us cover both of these during a workday. The first time we go to compliance.microsoft.com we will be greeted by a guide:
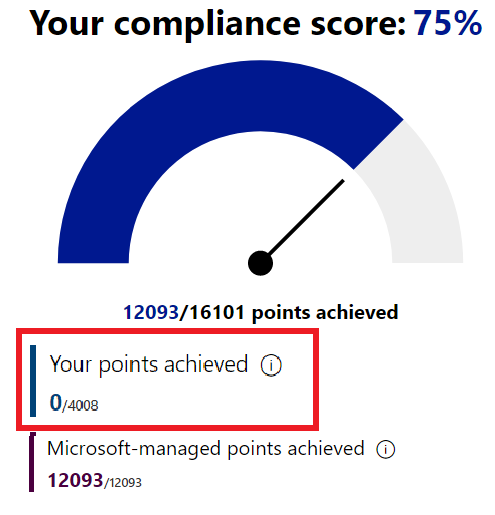
In our lab, we can see that Microsoft starts out with 75% (06.08.2020) before we have made changes. This might be different in your environment.
As you can see, with this new tenant, all the points comes from their side, and we have 0.
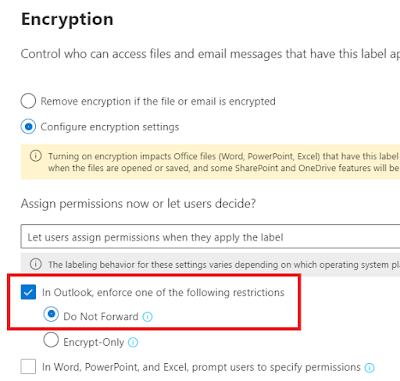
But the moment you start doing stuff, like create sensitivity labels, this will change:
Other useful tools
Microsoft has helped us out quite bit here, but that doesn’t make us safe, or immune to ransomware attacks. Even if we had a completely redundant organization it would be difficult to secure ourselves against that also being infected with ransomware. But using tools like Office 365 ATP with safe attachments, safe links and more can help. Also, Microsoft Defender ATP will be a huge help. Microsoft tells a story about bad rabbit, a ransomware that could have really exploded a few years back. When a user in Russia was infected, because he was using defender ATP, a protection against bad rabbit was up and running within minutes. That is the power of the cloud.Using the threat management dashboard actively can be a useful thing to start our day with.
https://protection.office.com/searchandinvestigation/dashboard A cup of coffee and a view of the world. My new and fresh tenant doesn’t say much about the dangers in my organization, but this view will change after a while and we will get a lot of useful information.
Best of luck out there and stay safe.
Best of luck out there and stay safe.






Comments
Post a Comment