A deeper dive into protecting your information in the cloud - Part 2
As we talked about in the first post, we have several ways to protect our information in the cloud. I thought it would be fitting to start with AIP. Azure Information Protection or MIP (Microsoft Information Protection) as some call it these days. But a lot has changed here, and we will start by describing what has happened lately. A fairytale from the real world . Feel free to ignore the history chapter if you want to go to the technical stuff. Fair warning: In this, our first post about AIP/MIP we will look at the basics of things, and how it all looks from the portal.
Not long ago we did our config in the Azure portal. We created our protection templates and labels in the AIP portion of the Azure portal, and we used the AIP client on our computers to use these labels either by using the right-click option Classify and Protect or by labeling documents and information in Office apps. We had a label ribbon that was installed with the clients and it worked okay…ish.
There were issues though, and one of the issues some discovered came sneeking in sideways. Or from the Office 365 portal to be more presise. You see, Microsoft decided to let us create labels there too. Shiny new labels from a new and fancy place. So some people created labels there, and some in the azure portal and suddenly we had chaos, because there was a problem with this approach. They were not aware of each other. AIP labels and the labels in the Office portal could do the same in a lot of areas, but the version of the client you downloaded would decide from which portal the settings were retrieved.
So what happened next, you ask? Well, this is where things started to be really complex. Microsoft made it possible to unify the two solutions. Unification ment that the config you did in either portal were visible in the other, and you could create labels in one of the portals and publish them in the other. So things were looking up for the people working with Information protection. But we still needed to use the appropriate client. If you wanted to reach the labels from the AIP portal you would use the AIP client, and if you wanted to retreive the settings from the Office 365 portal (Security and Compliance) you would use the AIP Unified Labeling client. If you want to read a little more about that, please check out this blog post.
We were also told (warned) that as soon as the labels in the Security and Compliance portal reached feature parity, we would no longer do any config in the AIP portal. Good, right? We wouldn't mess about in two portals anymore. (Yay! One less portal to have to think about) But there was one small issue. Where AIP labels could be used for others systems than Office 365, the sensitivity labels (In the office portal) were for data in Office 365. So, what about our on-premises systems? Or other cloud services? Or other storage? Well, we can use the sensitivity labels for other services, and for SQL, and for on-premises file servers etc. And in one of the next blogposts we will go into a method for using sensitivity labels for several cloud services. Microsoft Cloud App Security.
Today we have what we might call almost feature parity, And we even have a new AIP scanner (way to apply sensitivity labels to our on-premises file server and SharePoint) with the new sensitivity labels. So, where do we do our config? Security and Compliance portal you say? Well, you are right. We started out in the Security and Compliance portal. Which became the compliance portal and a different security portal. Which now is … The security and compliance portal, but a little different now. Selecting the security portal will get you there, and so will selecting the compliance portal.
This is where pressing the security button takes you:
While this is where pressing the compliance button takes you:
So … eh … I guess we are back, full circle to the security and compliance portal. Nice ey?
Well, enough history. There would be a lot more to say, but I know your not interested, and really just want to know how this stuff work. Or if it works.
This will be done in more than one part. This first one will (as mentioned before) be more of an overview of things in the portal. Entering the Security and Compliance portal, we can see some stuff mentioning Classification.
Looking at this bar on your left you will see some interesting stuff. (many interesting things, but we will look at two of them here).
Classification
This contains three submenus.
Sensitivity labels
Lets start with a small clarification. Labels in AIP/MIP is something you tag your information with. It is a way for you to classify your info by applying these tags, and the tags can contain information about the document for instance. So, if you have a document with confidential info for instance, you may want to classify the document as Confidential. At the same time you want to protect the data from being read by anyone who shouldn't. A sensitivity label can do these things. Both tag the document, and protect it (if that is what you want).
So, let us just say that sensitivity labels are the labels we use to classify and protect content. They will follow us around through Office etc. and can be used to classify and protect content in many different ways. We can label stuff from our Office apps, we can label stuff in SQL, we can let Cloud App security look through data and label them according to what info they contain and many more things. Two things to note here. We can create labels here, and we can publish them to our users. If we select to create a label, it will still not be visible to anyone. It is when we publish them they will be seen by the users we publish them to.
Retention labels
Retention labels is something quite different. Here we can also label our information, but in this case, we tell Office 365 how long a piece of info should be retained for, and what should be done with it after the retention periode is passed. We have different retention labels with different rules that can be applied based on what kind of information it is. Know that a document cannot have both a retention label and a sensitivity label.
Sensitive info types.
This might seem self explanatory, but basically Microsoft have created a bunch of sensitive info types, for instance Credit Card info, or Social Security number, so that you are able to find data that includes these sensitive info types and do different things with them. Like for instance protect them. These sensitive info types are found throughout Office and can be used through Office 365 Data Loss prevention and Microsoft Cloud App security for instance. We will take a closer look at both of these during this series. If you are unable to find any useful info types, you are welcome to create your own.
Information governance
The information governance panel gathers some of the information we need regarding labeling for instance. We have the following possibilities if we expand this:
Dashboard
Ah yes. The dashboard. We didn't use to have this, and it is a welcome feature indeed. This gives us unigue insight into how labels are applied in our organization for instance. It also has the Information Governance toolbox, which requires a little more detail:
The Infomation governance toolbox is new, and here we can do things like create/publish labels etc. As we saw earlier, we can also do this directly from the sensitivity labels/retention labels options, and that is also where selecting this from the toolbox, takes us.
Label activity explorer
This will show us the label activity in a certain time frame.
We skip the PST and Archiving parts, since this doesn't really have anything to do with Information protection and look at Rentention which is where we create and publish retention labels for instance:
Labels and label policies.
First of all, I am sorry this was so long, but it is difficult to make it shorter if we are going to cover it all. But thats it for now. This is all I thought I would include in this part 1 of AIP/MIP. I will continue to write about how we can use Information Protection, and in what systems. We will look at stuff like labeling info in Office and emails. SharePoint Online, SQL etc. I hope this has been useful and given an understanding of the basics of AIP/MIP.
Hope to see you next time!
A brief (and simplified) history of Information Protection
Not long ago we did our config in the Azure portal. We created our protection templates and labels in the AIP portion of the Azure portal, and we used the AIP client on our computers to use these labels either by using the right-click option Classify and Protect or by labeling documents and information in Office apps. We had a label ribbon that was installed with the clients and it worked okay…ish.
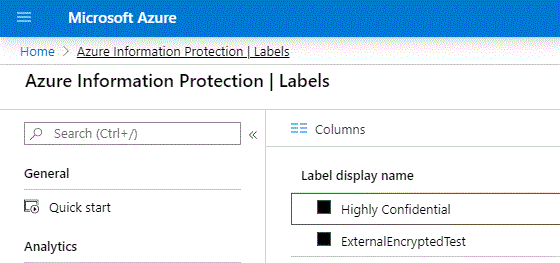 |
| Before |
There were issues though, and one of the issues some discovered came sneeking in sideways. Or from the Office 365 portal to be more presise. You see, Microsoft decided to let us create labels there too. Shiny new labels from a new and fancy place. So some people created labels there, and some in the azure portal and suddenly we had chaos, because there was a problem with this approach. They were not aware of each other. AIP labels and the labels in the Office portal could do the same in a lot of areas, but the version of the client you downloaded would decide from which portal the settings were retrieved.
So what happened next, you ask? Well, this is where things started to be really complex. Microsoft made it possible to unify the two solutions. Unification ment that the config you did in either portal were visible in the other, and you could create labels in one of the portals and publish them in the other. So things were looking up for the people working with Information protection. But we still needed to use the appropriate client. If you wanted to reach the labels from the AIP portal you would use the AIP client, and if you wanted to retreive the settings from the Office 365 portal (Security and Compliance) you would use the AIP Unified Labeling client. If you want to read a little more about that, please check out this blog post.
We were also told (warned) that as soon as the labels in the Security and Compliance portal reached feature parity, we would no longer do any config in the AIP portal. Good, right? We wouldn't mess about in two portals anymore. (Yay! One less portal to have to think about) But there was one small issue. Where AIP labels could be used for others systems than Office 365, the sensitivity labels (In the office portal) were for data in Office 365. So, what about our on-premises systems? Or other cloud services? Or other storage? Well, we can use the sensitivity labels for other services, and for SQL, and for on-premises file servers etc. And in one of the next blogposts we will go into a method for using sensitivity labels for several cloud services. Microsoft Cloud App Security.
Today we have what we might call almost feature parity, And we even have a new AIP scanner (way to apply sensitivity labels to our on-premises file server and SharePoint) with the new sensitivity labels. So, where do we do our config? Security and Compliance portal you say? Well, you are right. We started out in the Security and Compliance portal. Which became the compliance portal and a different security portal. Which now is … The security and compliance portal, but a little different now. Selecting the security portal will get you there, and so will selecting the compliance portal.
 |
| Eenie meenie miney mo |
This is where pressing the security button takes you:
 |
| Microsoft 365 security and compliance center |
While this is where pressing the compliance button takes you:
 |
| Microsoft 365 security and compliance center |
So … eh … I guess we are back, full circle to the security and compliance portal. Nice ey?
Well, enough history. There would be a lot more to say, but I know your not interested, and really just want to know how this stuff work. Or if it works.
How AIP/MIP works.
This will be done in more than one part. This first one will (as mentioned before) be more of an overview of things in the portal. Entering the Security and Compliance portal, we can see some stuff mentioning Classification.
 |
| Some stuff about information protection and classification. |
Looking at this bar on your left you will see some interesting stuff. (many interesting things, but we will look at two of them here).
Classification
This contains three submenus.
Sensitivity labels
Lets start with a small clarification. Labels in AIP/MIP is something you tag your information with. It is a way for you to classify your info by applying these tags, and the tags can contain information about the document for instance. So, if you have a document with confidential info for instance, you may want to classify the document as Confidential. At the same time you want to protect the data from being read by anyone who shouldn't. A sensitivity label can do these things. Both tag the document, and protect it (if that is what you want).
 |
| Labels and sublabels |
So, let us just say that sensitivity labels are the labels we use to classify and protect content. They will follow us around through Office etc. and can be used to classify and protect content in many different ways. We can label stuff from our Office apps, we can label stuff in SQL, we can let Cloud App security look through data and label them according to what info they contain and many more things. Two things to note here. We can create labels here, and we can publish them to our users. If we select to create a label, it will still not be visible to anyone. It is when we publish them they will be seen by the users we publish them to.
Retention labels
Retention labels is something quite different. Here we can also label our information, but in this case, we tell Office 365 how long a piece of info should be retained for, and what should be done with it after the retention periode is passed. We have different retention labels with different rules that can be applied based on what kind of information it is. Know that a document cannot have both a retention label and a sensitivity label.
Sensitive info types.
This might seem self explanatory, but basically Microsoft have created a bunch of sensitive info types, for instance Credit Card info, or Social Security number, so that you are able to find data that includes these sensitive info types and do different things with them. Like for instance protect them. These sensitive info types are found throughout Office and can be used through Office 365 Data Loss prevention and Microsoft Cloud App security for instance. We will take a closer look at both of these during this series. If you are unable to find any useful info types, you are welcome to create your own.
Information governance
The information governance panel gathers some of the information we need regarding labeling for instance. We have the following possibilities if we expand this:
 |
| Information governance |
Ah yes. The dashboard. We didn't use to have this, and it is a welcome feature indeed. This gives us unigue insight into how labels are applied in our organization for instance. It also has the Information Governance toolbox, which requires a little more detail:
 |
| The dashboard |
The Infomation governance toolbox is new, and here we can do things like create/publish labels etc. As we saw earlier, we can also do this directly from the sensitivity labels/retention labels options, and that is also where selecting this from the toolbox, takes us.
 |
| Information governance toolbox |
Label activity explorer
This will show us the label activity in a certain time frame.
 |
| We can now see our label activity. |
Labels and label policies.
 |
| Labels and label policies. |
First of all, I am sorry this was so long, but it is difficult to make it shorter if we are going to cover it all. But thats it for now. This is all I thought I would include in this part 1 of AIP/MIP. I will continue to write about how we can use Information Protection, and in what systems. We will look at stuff like labeling info in Office and emails. SharePoint Online, SQL etc. I hope this has been useful and given an understanding of the basics of AIP/MIP.
Hope to see you next time!


Comments
Post a Comment