Protection, permissions and the "Add any authenticated users" option
Sharing is caring they say, and when we work with AIP, we must often consider how to configure labels to use for sharing internally and externally.
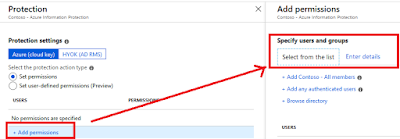
When you add protection to your label, you need to add permissions as a part of the configuration. You have two options: Select from the list or Enter details:
If you choose to enter details, you have a lot of freedom, and can specify whoever you want, or what domain you want. The other option: Select from the list let's you add a user or group (or several) from your organization (or every member of your Azure AD), or you can use the "Any authenticated users" option. That is the one we will look at today.
By selecting "Any authenticated users" option you say that any user who has an email account that is authenticated by Azure AD or a federated social provider, or who is authenticated with a Microsoft account or uses a one time passcode can access the content.
If you think about that for a moment you might see how this is similar to the "Encrypt/Encrypt-Only" option where the email is encrypted and recipients must be authenticated, but then they have all usage rights except Save As, Export and Full Control (Basically means no restriction except that they cannot remove the protection). And yes, like the Encrypt option the "Any authenticated users" setting doesn't restrict who can access the content that the labels protects. The content will be encrypted but using this option you are provided with the possibility to restrict how the content can be used and accessed.
 |
| Restrict or give full access. It is up to you. |
Another advantage with this one compared to the Encrypt option is that this is AIP and not OME. You will therefore also be able to track and revoke the content so there are definately use cases for it. Microsoft suggests a couple of scenarios for this here: More information about add any authenticated users
- You don't mind who views the content, but you want to restrict how it is used. For example, you do not want the content to be edited, copied, or printed.
- You don't need to restrict who accesses the content, but you want to be able to track who opens it and potentially, revoke it.
- You have a requirement that the content must be encrypted at rest and in transit, but it doesn't require access controls.



Comments
Post a Comment