Can Information Protection help us against Ransomware?
We have many useful tools against ransomware in Microsoft 365, but can Information Protection be one of them? My good friend Olav Tvedt took up this question the other day, and the inititial answer is no. But the again, it can also be yes, in a way. This is not something I have tested, but it is an interesting theory. Encryption will not stop ransomware from re-encrypting the data, but there is another thing it can do, that might have helped quite a few of the victims lately.
One of the awesome things about Information Protection is the way it protects data with the use of AAD authentication. We allow or deny people the access rights to a piece of information by their AAD accounts. And this is where we get a useful tool against ransomware. Not the attack itself, but what has been done to victims lately, where they have been threatened with getting sensitive data released to the dark web after the attack. For some this can be devastating, and this is where Information Protection can help us.
Disclaimer: This would only work if the data thieves would not be able to decrypt the data before they are caught. This is where our logging works in our favor. For the eager admins who pay attention through logs, MCAS and more, it would be very visible if someone did mass de-cryptions etc.
How can it help?
As mentioned over, Information Protection encrypts data and allows people access, based on their AAD mail-enabled user account. When we are exposed to a ransomware attack, the attackers will have access to an account as well (or more) and one of the first things we do is make sure user accounts are secured, maybe by changing passwords, enforcing MFA and other tools. If we have protected our sensitive data, this also means that the attackers will no longer have access to the data when we remove access to the users. To make sure of this we use a couple of pretty cool features in Information Protection:
Picture 1 - To make this work, we of course need to encrypt our info.
The first of the two, is also the less restricted one in a way, but in another way if we look away from ransomeware it can be more restricted, in the way that we will loose access to the data after a while, and would need to re-share them if we want others to still have access to the data. Also, see how it says a number of days after the label has been applied, not after someone has opened it. Useful in many cases, but certainly not in all.
Using this option would stop people from being able to access the data after a data or number of days, but may not be the perfect option for our use case. For data that is not very sensitive, it might still be enough.
The second option is for our most sensitive data. It makes sure we need to verify our credentials with AAD everytime we open the data. In this case it would be completely useless for our data thieves if they got their hands on it.
Picture 3 - Never allow offline access = Always authenticate.
This might be a little disruptive for people who want to read the data offline for instance, but for our most sensitive data, it might still be worth it?
I will repeat that I have not had the chance to test this myself, but the theory is that this would be a useful tool against data thieves and ransomware actors. If you have had experience with this, please let me know in the comments.



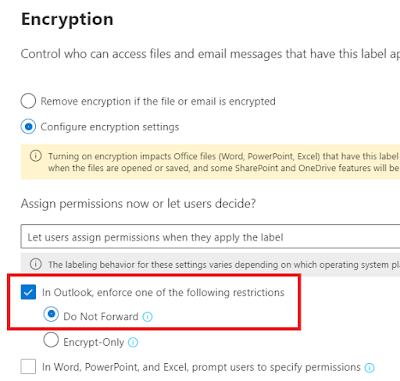


Interesting points, and definitely something to consider when taking measures to reduce data leakage and increasing protection against ransomware!
ReplyDelete